Blockchain Forensics Made Simple: How to Trace and Stop Stolen Crypto Funds

Source: Blockchain Forensics: A Practical Guide to Tracing Stolen Funds
Cryptocurrency’s explosive growth has unlocked new financial opportunities but also ushered in a wave of digital crime. Since 2016, an average of $1.3 billion in crypto assets have been stolen annually via hacks, scams, and exploits - from vulnerable smart contracts to bridge breaches. Despite blockchain's inherent transparency, global enforcement struggles because attackers exploit regulatory gaps and use complex laundering techniques.
This guide breaks down blockchain forensic investigation fundamentals and advanced strategies, offering developers, founders, and security researchers a structured approach to tracing stolen funds and mapping attacker behavior step-by-step.
1. Understanding the Web3 Threat Landscape
The crypto space attracts a variety of sophisticated threats, evolving far beyond early phishing scams into:
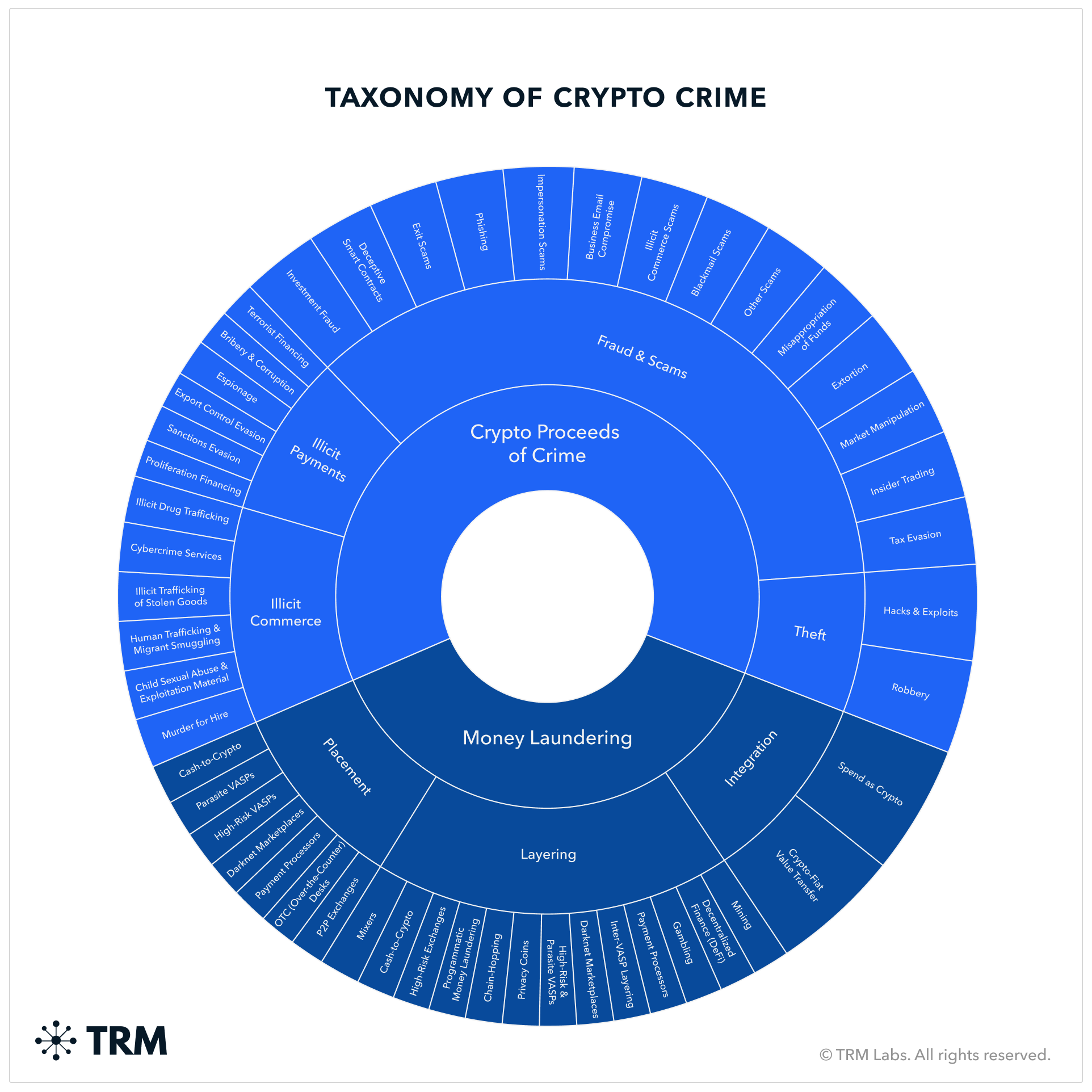
- Protocol vulnerabilities exploited via flash loans or flawed logic
- Bridge hacks draining assets by bypassing cross-chain validation
- Automated wallet drainers and scam token contracts
- Phishing and front-end compromises targeting user trust
- Nation-state cybercrime, with groups like Lazarus (DPRK) and Gonjeshke Darande (Predatory Sparrow) linked to regional attacks
The scope and mechanics of these attacks require specialized knowledge in blockchain forensics.
2. What Is Blockchain Forensics?
Blockchain forensics involves analyzing on-chain data to follow the flow of funds, detect illicit activity, and derive actionable insights. Unlike traditional investigations relying on private bank records, blockchain forensics operates on public, immutable ledgers, enabling transparent tracing of transactions globally.
Key features:
Uses of Blockchain Forensics:
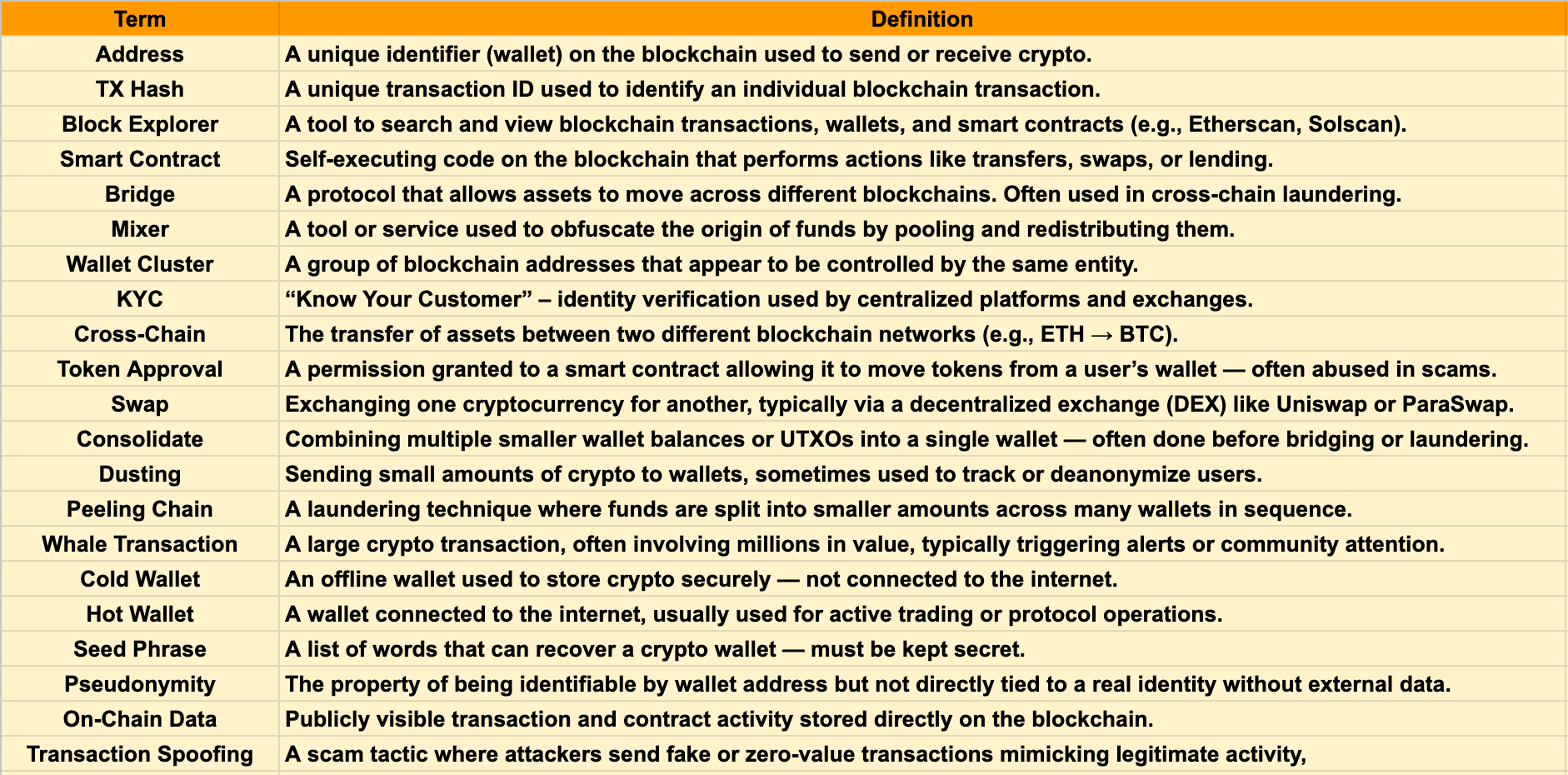
- Transparency: Every transaction is recorded and traceable.
- Pseudonymity: Wallets are not directly linked to real identities, requiring behavioral clustering and OSINT.
- Immutability: Data cannot be changed or erased, ensuring evidence integrity.
- Global Access: Anyone can inspect the ledger irrespective of geography.
- Tracking stolen funds post-exploit
- Identifying laundering patterns like mixers and peel chains
- Monitoring scam tokens and rug pulls
- Supporting AML and compliance in exchanges and protocols
- Assisting law enforcement and security teams with attribution and recovery
3. Investigative Methodology: Step-by-Step
Step 1: Detecting On-Chain Exploits and Theft
Identify suspicious activity by recognizing transaction anomalies such as:
- Large, unexpected outflows from treasury wallets
- Token swaps in governance or staked assets
- Approvals to suspicious contracts
- Fund bridging to obscure chains
- Dormant wallets suddenly active or rapid fund dispersal across multiple wallets
Sources for early detection include:
Case Example: Bybit Hack (February 21, 2025)
- Specialized monitoring firms (e.g., PeckShield, SlowMist, CipherTrace)
- Independent blockchain researchers (e.g., 0xB2dF, ZachXBT)
- Public blockchain explorers (Etherscan, Solscan)
- On-chain analytics platforms (Arkham Intelligence, Debank)
- $1.46B stolen from an Ethereum cold wallet
- Exploit bypassed signature validation via spoofed Safe UI, not a private key leak
- Attacker gained control by manipulating smart contract logic through a disguised transaction interface
- Independent investigators quickly identified and alerted the community ([IMAGE_3])
Step 2: Define the Scope
Clearly frame your investigation:
- Nature of incident (exploit, scam, laundering)
- Financial scale versus resource commitment
- Tooling availability across blockchains involved
- Potential collaboration and legal considerations
Focus on high-value wallets or early fund movements in large-scale incidents for manageability.
Step 3: Data Collection & Enrichment
Gather essential on-chain data such as:
- Wallet addresses involved (victims, attackers, intermediaries)
- Transaction hashes (exploits, swaps, bridges)
- Smart contract details and event logs
- Token types and amounts
- Timestamps for event sequencing
Add context through enrichment:
- Is the wallet reused from past incidents?
- Known laundering behaviors in transaction patterns
- Any links to mixing services or bridges?
Bybit example data:
- Victim wallet: 0x1Db9...FCF4
- Attacker wallet: 0x4766...86E2
- Labels and transaction logs structured for clarity [IMAGE_4],[IMAGE_5]
Step 4: Transaction Tracking
Follow stolen funds through:
- Immediate asset swaps into non-freezable tokens
- Splitting funds into multiple wallets to obscure origins ("peel chains")
- Monitoring dormancy and reactivations
- Identifying mixing services and cross-chain bridges
Set real-time alerts for suspicious wallet activity.
Bybit post-theft activity:
- StETH and mETH tokens funneled through newly created wallets, swapped on decentralized protocols like ParaSwap and BreederDodo to avoid centralized blacklisting [IMAGE_6]
- Mantle protocol’s withdrawal delay blocked $15,000 cmETH laundering
- ETH split into 40 transactions of 10,000 ETH each for laundering obfuscation
Step 5: Chain Analysis
Delve deeper to:
- Group addresses controlled by the same actor (clusters)
- Map laundering infrastructure (DEXes, mixers, bridges)
- Detect patterns in transaction timing and gas usage
- Identify relationships between known threat actors and wallets
Tools combine blockchain data and OSINT to profile attackers and surface linked wallets.
ZachXBT linked Bybit attacker wallets to Lazarus group activities and past hacks on Poloniex, Phemex, and BingX, noting repeat laundering infrastructures and patterns [IMAGE_7 - 10].
Bybit funds were largely moved from Ethereum to Bitcoin through bridges like Thorchain and eXch before being mixed using CoinJoin and centralized Bitcoin mixers to frustrate tracing.
Common Laundering Methods:
- Chain hopping: Moving assets across blockchains for obfuscation; often from Ethereum to low-regulation chains like BNB or Tron [IMAGE_11]
- Mixing services: Tumbling coins through pools (decentralized or custodial) such as Tornado Cash or Wasabi Wallet [IMAGE_12]
- Peel chains: Breaking down large balances into many small transactions over time
- Off-ramping: Using P2P platforms or OTC brokers for fiat exchange outside regulated venues
- Unregulated exchanges: Platforms that tolerate or ignore KYC to enable cash-outs (e.g., Huione, Xinbi, Grantex)
Step 6: Collaborate and Validate
- Work with trusted investigators through Telegram, private Discord servers, or secure platforms
- Confirm behavioral patterns using multiple tools and intelligence sources
- Document evidence and reasoning clearly to support attributions and actionable outcomes
Step 7: Build Profiles and Report Findings
Produce concise, clear reports including:
- Incident summary and timeline
- Wallet clusters and transaction charts
- Infrastructure used and laundering tactics
- Evidence-backed attribution to threat actors where possible
- Recommendations for exchanges, law enforcement, or security teams
4. Challenges in Blockchain Forensics
Key barriers include:
- Jurisdictional complexity: Cross-border enforcement is slow and inconsistent
- Privacy tools: Mixers and privacy wallets severely hinder traceability
- Cross-chain complexity: Rapid bridging between numerous blockchains adds blind spots
- Pseudonymity: Difficulty in linking addresses to real identities without external data
- Limited tooling: Emerging chains may lack forensic infrastructure
- Uncooperative platforms: Some centralized exchanges ignore freeze requests
- Automated laundering scripts: Fragmentation and obfuscation occur at machine speed
- Evolving attacker tactics: Continuous adaptation requires ongoing learning
5. Analysis of Stolen Funds and Laundering Methods
After theft, attackers focus on:
Popular laundering tactics:
- Obfuscating origins through mixers and multi-wallet layering
- Breaking forensic linkages using token shuffles and DEX swaps
- Evading detection by dispersing funds rapidly and timing attacks strategically
- Converting to stablecoins or blue-chip tokens for liquidity and ease of off-ramping
- Monitoring investigator reactions on social platforms for tactical adjustments
- Chain hopping to less-monitored or low-liquidity blockchains
- Mixing services that pool and redistribute funds anonymously
- Peel chains transferring funds through many small hops
- P2P and OTC brokers facilitating off-chain liquidation to fiat
- Unregulated exchanges offering weak compliance as exit points
Conclusion
As the crypto ecosystem advances, so do the sophistication and scale of illicit activity. Blockchain forensics is a critical tool to trace stolen assets, expose laundering infrastructure, and link threat actors - but it demands persistent investigation, collaborative intelligence sharing, and coordinated cross-jurisdictional action.
By mastering forensic techniques and staying ahead of emerging laundering methods, the community can tighten defense lines and boost accountability - making crypto safer and more transparent.
Stay updated with the latest blockchain security insights by subscribing to SomaXBT.


