Crypto Hacks Hit $3.1B in 2025 as Access Flaws Fuel Rising Losses
Source: CoinTelegraph
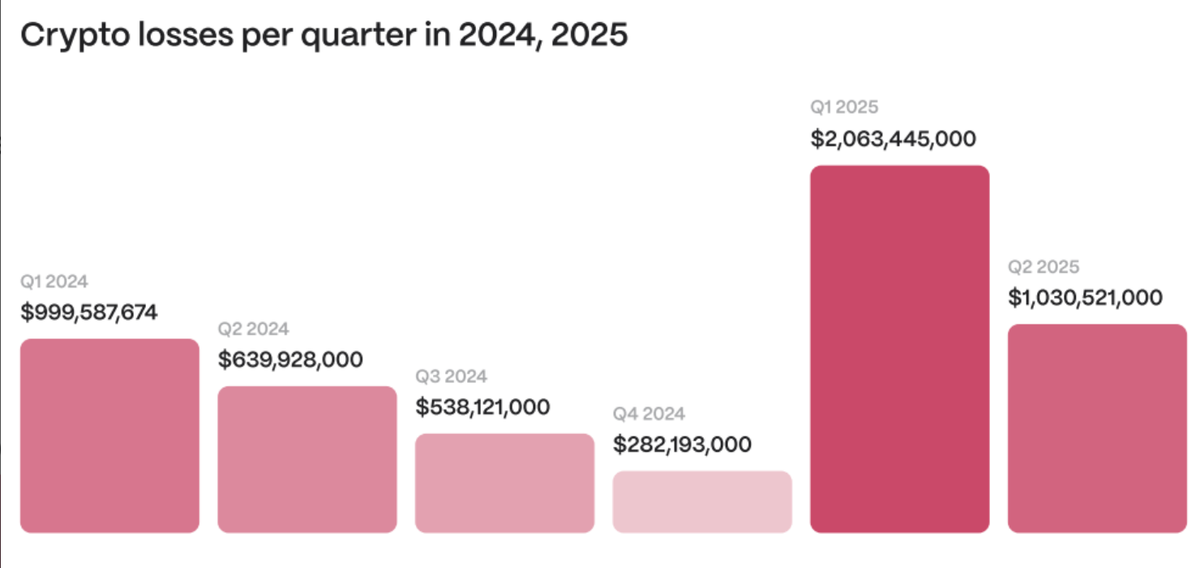
The blockchain security firm Hacken reports that crypto-related losses in the first half of 2025 have already surpassed $3.1 billion. This exceeds the total $2.85 billion lost throughout 2024. While the massive $1.5 billion Bybit breach early this year is a notable event, the wider cryptocurrency landscape continues to struggle with serious security flaws.
good here
Key Points of Losses
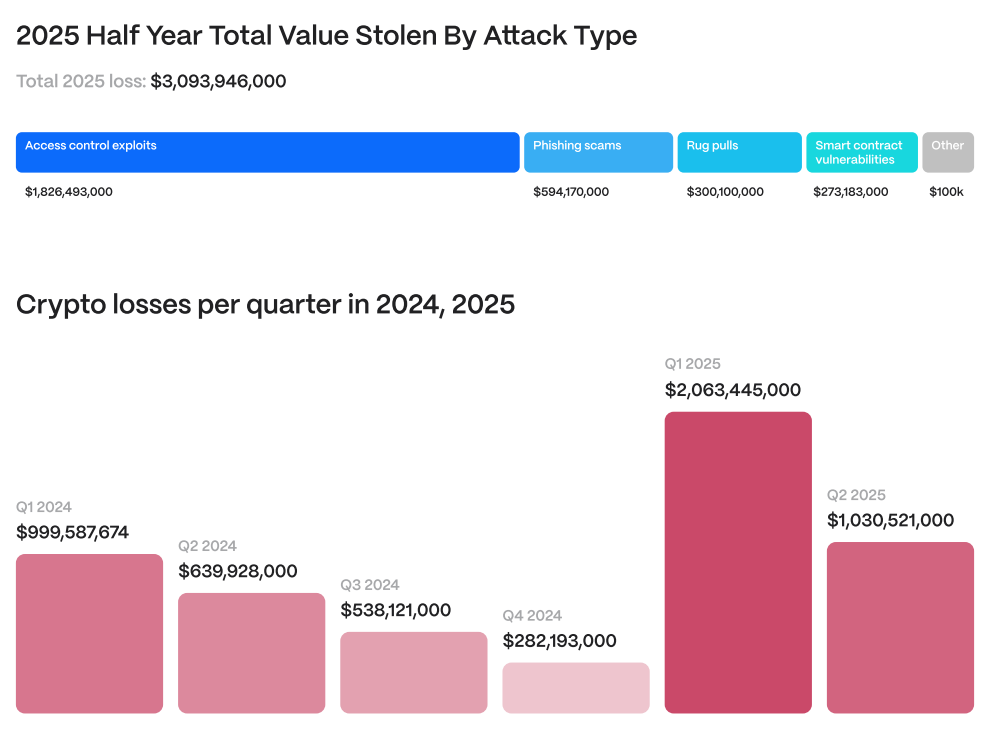
Shift in Attack Strategies
- Access-control vulnerabilities are the leading cause, making up about 59% of total losses.
- Smart-contract bugs led to around 8% of the losses, approximately $263 million stolen.
As the crypto ecosystem matures, attackers are increasingly exploiting human errors and operational weaknesses rather than purely technical cryptographic flaws. Current tactics include:
- Blind signing attacks
- Private key leaks
- Complex phishing schemes
This trend indicates that access control remains one of the weakest security links in the industry, even with evolving technical defenses.
Operational Failures Dominate Losses
In total, operational security breaches-a category involving both decentralized finance (DeFi) and centralized finance (CeFi) platforms-accounted for $1.83 billion stolen. The largest event in Q2 2025 was the Cetus hack, in which $223 million vanished within 15 minutes, marking it as DeFi’s worst quarter since early 2023. This attack also interrupted a five-quarter downward trend in DeFi exploits.
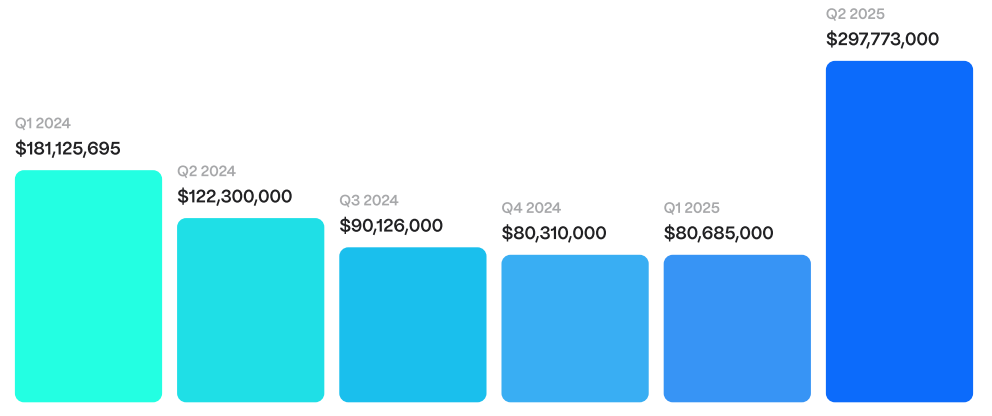
During Q4 2024 and Q1 2025, access-control failures mostly overshadowed bugs. However, Q2 saw a sharp drop in access-control losses within DeFi to $14 million-its lowest since Q2 2024-even as smart-contract exploits rose.
The Cetus breach exploited a vulnerability in liquidity overflow checks. The attacker employed a flash loan to open tiny positions and drained funds across 264 pools. Hacken suggests that real-time monitoring of total value locked (TVL) with automatic pause mechanisms could have saved up to 90% of the stolen assets.
AI Integration Brings New Security Challenges
Artificial intelligence (AI) and large language models (LLMs) are now deeply embedded in Web2 and Web3 applications. While fueling innovation, this expansion also creates new attack vectors:
- AI-related exploits surged by 1,025% compared to 2023.
- Nearly 99% of these incidents are linked to vulnerabilities in insecure APIs.
- Five new AI-related Common Vulnerabilities and Exposures (CVEs) were added recently.
- About 34% of Web3 projects utilize AI agents in live settings, increasing their exposure to AI-targeted attacks.
Current cybersecurity standards like ISO/IEC 27001 and NIST’s Cybersecurity Framework fall short of addressing AI-specific threats such as:
- Model hallucinations
- Prompt injection attacks
- Adversarial data poisoning
Industry experts agree that these frameworks must adapt to include governance addressing AI’s unique risks.
Stay informed about the latest trends and risks in Web3 security to safeguard your projects and investments.


