How to Drain a Lending Protocol Using a New Collateral Asset: A Step-by-Step Exploit Explained

Source: kankodu
A recent security issue was discovered in the lending protocol @vesuxyz, which is built in Cairo and supports multiple lending pools with various collateral-debt asset pairs. This vulnerability was responsibly reported through Immunefi’s bug bounty program and classified as High severity.
Here’s a clear breakdown of the flaw and how it was resolved.
About the Protocol
- @vesuxyz allows multiple isolated lending markets (pools).
- Each pool can set different borrowing limits via _max LTV_ (loan-to-value) ratios.
- The active Genesis pool uses a rehypothecation model similar to traditional lending markets.
- The security flaw arises specifically when a new asset is added as collateral.
The Exploit in Simple Terms
The attack drains the entire pool’s assets in three main steps by manipulating the way collateral shares are minted and their value is calculated.
Step 1: Exploiting Collateral Shares to Inflate Their Value
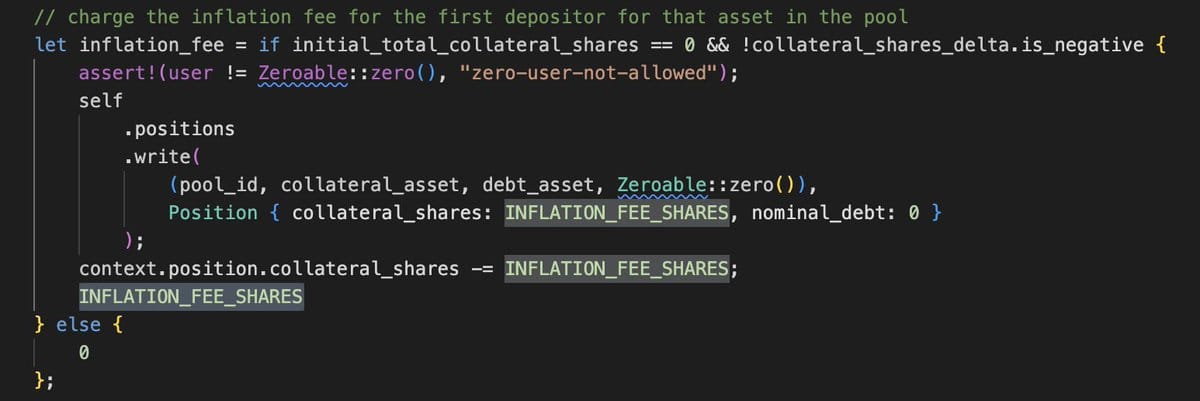
- When total collateral shares in a vault are zero, the protocol typically mints 1000 shares to a dead address to prevent “vault share inflation attacks” - this is designed to make inflation attacks expensive and unattractive.
- However, the protocol mints collateral shares as protocol fees when lenders earn interest. Unlike the initial minting to a dead address, this inflates total shares without the usual safety check.
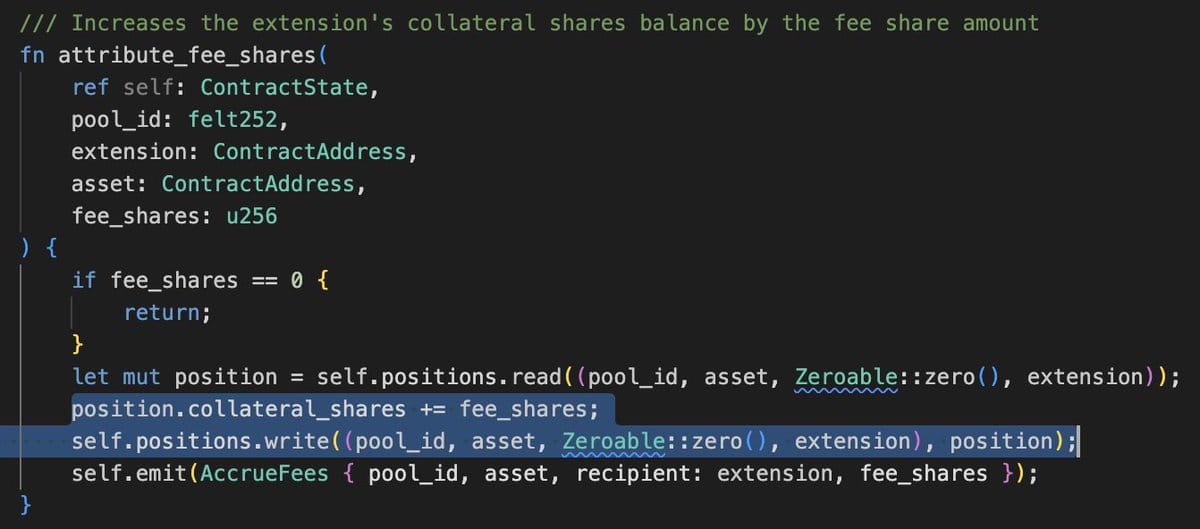
- An attacker can:
- Donate a small amount to the reserve while total shares are zero.
- Borrow this small collateral repeatedly and accumulate less than 500 wei worth of protocol fee shares.
- This causes total shares to become non-zero legitimately.
- Once total shares are non-zero, the attacker can mint a tiny amount of shares (less than 500 wei) and donate a large amount of collateral, dramatically increasing the value of these tiny shares.
Step 2: Borrowing Against Inflated Collateral
- With shares artificially boosted in value, the attacker can borrow the entire protocol’s assets collateralized by these tiny but now valuable shares.
How the Team Fixed It
- The issue has been patched - details shared by the team on their fix can be found here.
- The fix was audited, and the audit report is publicly available here: Audit Report.
What This Means for Developers and Founders
- Adding a new collateral asset without thorough checks can introduce unexpected vulnerabilities.
- Pay careful attention to total shares accounting and minting logic around protocol fees.
- Ensure audit trails include scenarios where shares can move from zero to non-zero states without usual inflation protections.
- Continuous bug bounty engagement like @vesuxyz’s partnership with Immunefi is vital for spotting high-risk issues early.
Stay vigilant and always audit changes carefully when introducing new collateral types to avoid similar share inflation exploits targeting lending protocols.


