Ongoing Supply Chain Attack Hits CrowdStrike npm Packages - Urgent Security Alert
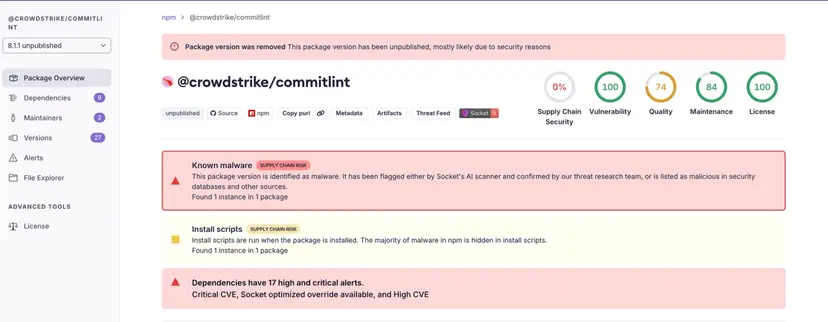
Source: socket.dev - Ongoing Supply Chain Attack Targets CrowdStrike npm Packages
A persistent supply chain attack, dubbed the “Shai-Halud” campaign, has escalated with multiple CrowdStrike npm packages now compromised. This campaign, first linked to Tinycolor and over 40 other npm packages, uses malicious code to stealthily seek and steal sensitive credentials from developers and CI/CD environments.
What’s Happening?
- Attackers injected a
bundle.jsscript that:- Runs TruffleHog, a legitimate tool that scans for secrets.
- Searches for tokens and cloud credentials on infected systems.
- Validates the credentials it finds using npm and GitHub APIs.
- Creates unauthorized GitHub Actions workflows in repositories.
- Exfiltrates stolen data to a hardcoded webhook endpoint.
- This malicious workflow file, named
shai-hulud.yaml(referencing sandworms from Dune), indicates intentional branding by the attacker. - The malware also:
- Looks for environment variables such as
GITHUB_TOKEN,NPM_TOKEN,AWS_ACCESS_KEY_ID, andAWS_SECRET_ACCESS_KEY. - Attempts to extract short-lived cloud credentials from build agents.
- Once the workflow is installed in a repo's
.github/workflowsdirectory, it can repeatedly send sensitive data during future CI runs.
- Looks for environment variables such as
Impacted Packages
Several CrowdStrike npm packages and versions have been confirmed compromised. The npm registry has removed the affected versions quickly, but the attack surface continues to expand, with more packages still under investigation.
What Steps Should You Take?
- Uninstall or pin dependencies to trusted versions immediately.
- Audit all environments (developer machines, CI/CD systems) that use these packages for signs of unauthorized publishing or stolen credentials.
- Rotate exposed tokens and secrets, especially if npm publishing rights were on compromised machines.
- Keep an eye on logs for suspicious
npm publishor package modification activities.
Indicators of Compromise (IOCs)
- Malicious file
bundle.jsSHA-256 hash:46faab8ab153fae6e80e7cca38eab363075bb524edd79e42269217a083628f09 - Data exfiltration endpoint:
hxxps://webhook[.]site/bb8ca5f6-4175-45d2-b042-fc9ebb8170b7
A detailed technical breakdown and remediation guide are forthcoming as the investigation proceeds.


