SuperRare’s $730K Hack Could’ve Been Prevented by Simple Testing, Experts Say
Source: SuperRare $730,000 Exploit Was Easily Preventable, Experts Weigh In | CoinTelegraph
NFT trading platform SuperRare was hit by a $731,000 theft after a critical error was discovered in its staking contract. Experts agree this vulnerability was basic enough to have been identified and stopped with routine security practices.
What Happened?
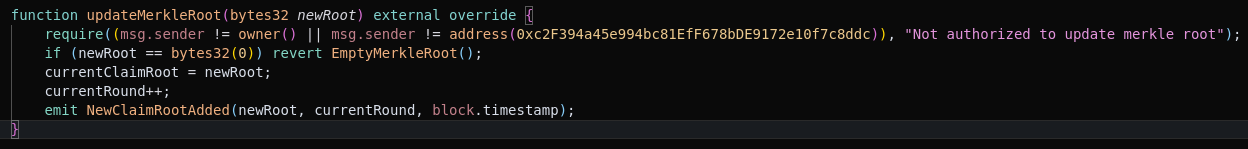
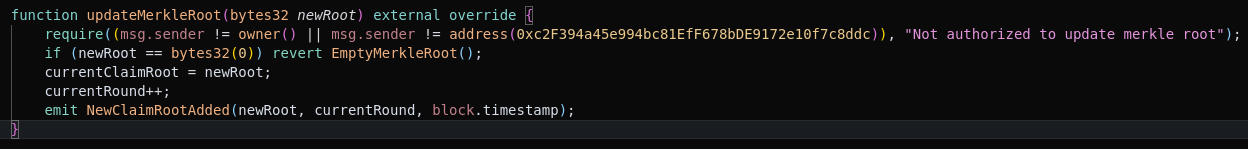
- The issue was in SuperRare’s staking contract, specifically a function controlling who can update the Merkle root - a data structure vital for tracking user staking balances.
- The smart contract was supposed to restrict this function to certain addresses.
- Instead, the logic was reversed, allowing anyone to call the function and manipulate the Merkle root, enabling attackers to withdraw staked tokens illicitly.
How Obvious was the Flaw?
- 0xAw, lead dev at Base DEX Alien Base, said this error was so clear “ChatGPT would’ve caught this.”
- Testing by CoinTelegraph confirmed that OpenAI’s o3 model correctly flagged the vulnerability.
- “Any competent Solidity developer would have spotted this,” 0xAw stressed.
- The bug essentially granted everyone access when it should have allowed only specific addresses.
Impact and Response
- Around 61 wallets were affected.
- SuperRare co-founder Jonathan Perkins assured that no core protocol funds were lost and impacted users will be reimbursed.
- Perkins said, “We’ve learned from this,” and promised tighter review processes for any future updates.
Expert Analysis & Lessons Learned
- A senior engineer at Nexus Mutual pointed out that unit tests would have caught this straightforward mistake.
- Mike Tiutin, CTO of AMLBot, called it a “silly developer mistake” that highlights the need for comprehensive test coverage.
- AMLBot CEO Slava Demchuk emphasized this as a classic case demonstrating why rigorous smart contract audits and testing are indispensable.
- Demchuk added the absence of bug bounty programs and thorough pre-deployment testing contributed to the failure.
- Perkins admitted that although the contracts were audited and unit-tested, this bug was introduced late and missed by final tests.
Why Unit Tests Matter
- Unit tests are small automated checks for individual parts of code (functions or methods).
- By verifying whether certain addresses can interact with sensitive functions, unit tests would have prevented this flaw.
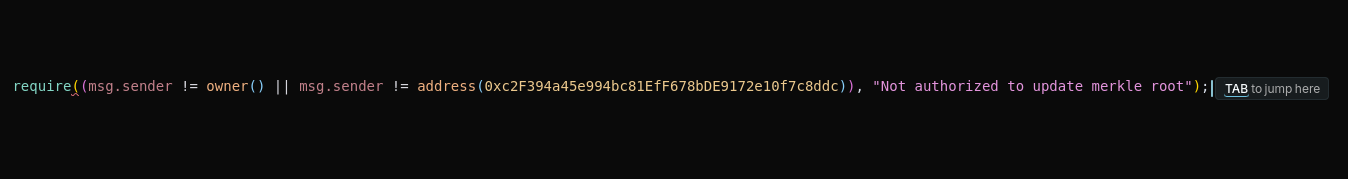
- The reversing of conditional logic in the staking contract’s permission check caused the serious vulnerability.
- As Demchuk put it, “an avoidable vulnerability that cost massively.”
Moving Forward: Improved Security Practices
- SuperRare now mandates re-audits for all post-audit code changes, no matter how minor, per Perkins.
- 0xAw called the original bug “a normal human error,” but criticized its unchecked deployment as a “monumental mistake.”
- The consensus remains that many critical vulnerabilities stem from simple, preventable oversights like this one.
Final Thoughts from Security Experts
- Yehor Rudytsia, head of incident response at Hacken, stated the bug was “pretty obvious” and could easily be caught through thorough testing.
- This incident serves as a reminder that even widely trusted projects can falter without stringent audit and testing protocols.
Stay updated on Web3 security incidents to learn from these mistakes and prevent similar oversights in your projects.


