The Longest Hack I’ve Ever Seen

🏴☠️ DEEP DIVE: Complex Hack of Abracadabra Vault.
We are Security Researchers.
Our goal is simple.
Find flawed patterns, buggy invariants.
Nothing, but pure understanding of the system first.
But what if the exploit and critical vulnerability consist of multiple steps?
4 , 5 , 6, 7 steps?? How to catch them all? Is it possible?
It's scary.
I thought in the past.
But once you understand the core of the flawed invariant, you immediately start to think.....
- What it can lead to?
- What's the state I can achieve by "kissing" this vulnerability?
And from there, your imagination start to work heavily.
Today, I want you to show brilliant example, how one broken invariant lead to multiple steps attack.
Smooth. Concise. Professional
Take popcorn and enjoy.
Abracadabra....
Hack.
⚙️ Key Concepts
Borrow Shares = fixed units representing debt (base)
Borrow Assets = actual debt amount (elastic)
When a user borrows, the protocol mints borrow shares based on the ratio:
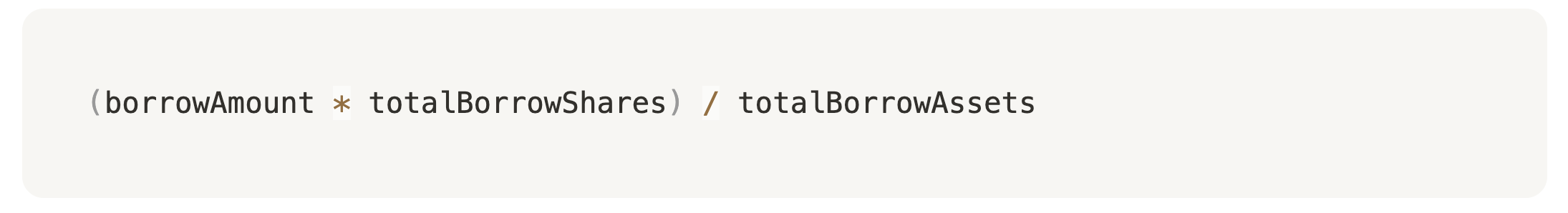
As interest accrues:
totalBorrowAssetsincreasestotalBorrowSharesstays the same
→ So, each share now represents more debt.
🔁 repayForAll() — The Core Mechanism
The protocol includes a special function: repayForAll()
It lets anyone repay everyone’s debt.
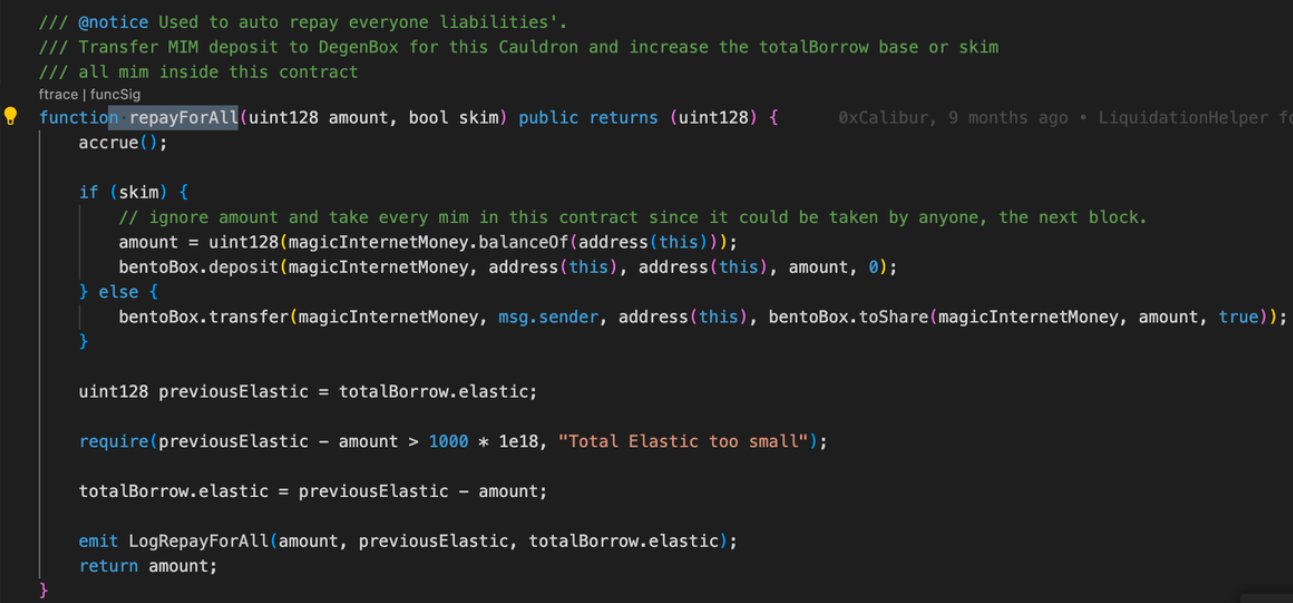
But here’s the trick:
totalBorrowAssets↓ when repaidtotalBorrowShares❌ doesn’t change
This imbalance is central of the exploit.
🧨 Breakdown of the Attack
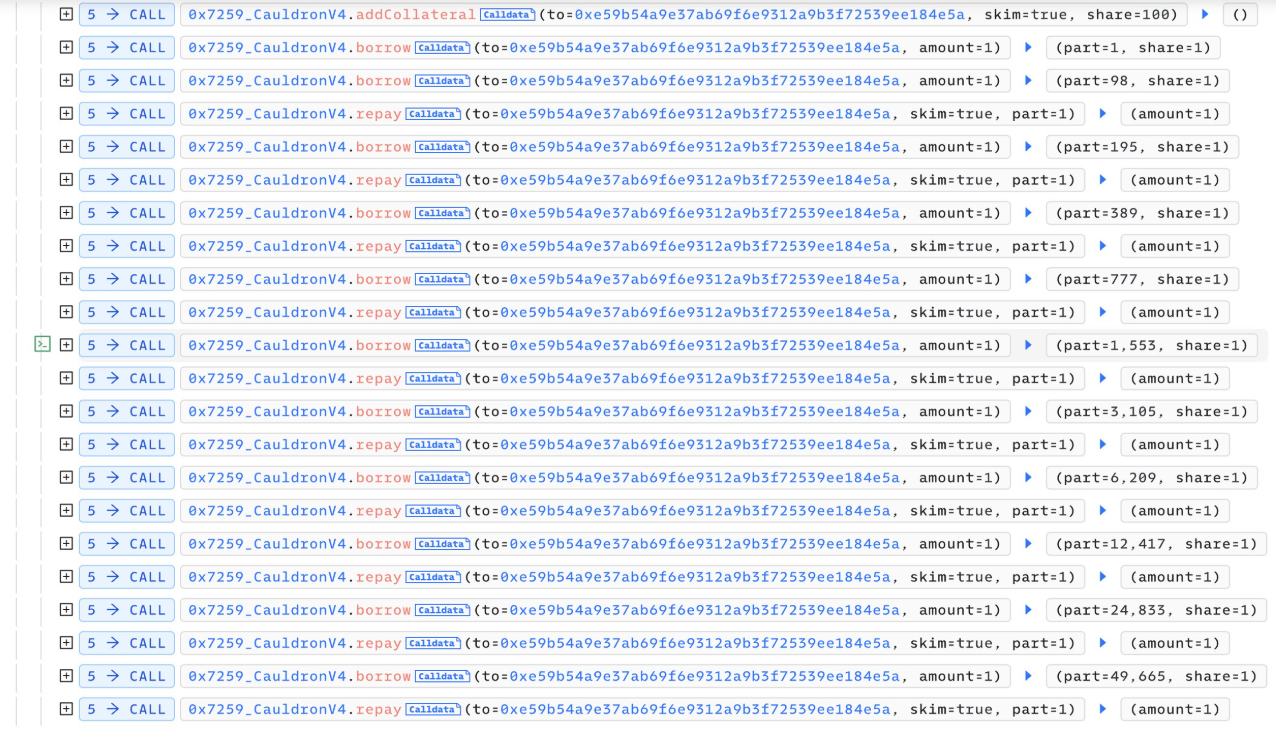
1. Flashloan + repayForAll()
Attacker starts with a flashloan, then calls repayForAll() multiple times.
This drives the system to a in-balanced state — ends with a 1:26 asset/share ratio.
✅ However, there’s a safeguard:totalBorrowAssetsmust stay > 1000 ETH
Once it drops below → switch strategy.
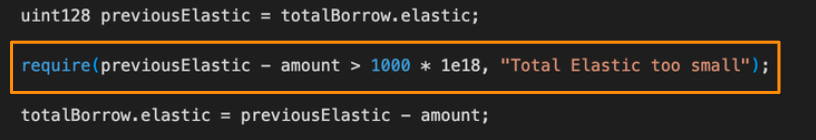
2. Switching to repay()
After hitting the 1K ETH threshold, attacker starts using repay() directly.
Unlike repayForAll, repay() reduces both:
totalBorrowAssetstotalBorrowShares

For the final borrower, attacker leaves just 100 wei of shares unpaid.
📉 Final state:
totalBorrowedAssets= 3totalBorrowShares= 100
3. Share Inflation Begins
At this step, we end up totalBorrowedAssets being 3 wei.
Now, we need to decrease it till 0
Attacker repays 1 wei of shares — three times.
Each time:
totalBorrowAssetsdropstotalBorrowSharesalso drops
📉 New state:
totalBorrowedAssets= 0totalBorrowShares= 97
This sets up the core inflation loop.
4. Looping the Exploit
Now the real abuse starts:
Attacker:
- Puts up minimal collateral (e.g. 100 wei)
- Borrows 1 wei of assets
- Repays 1 wei of shares
- Repeats… In the loop
Why it works:
totalBorrowAssets= 1totalBorrowShares= high
So, it means that during the borrowing of 1 wei of assets, huge value of borrowing shares is minted.:
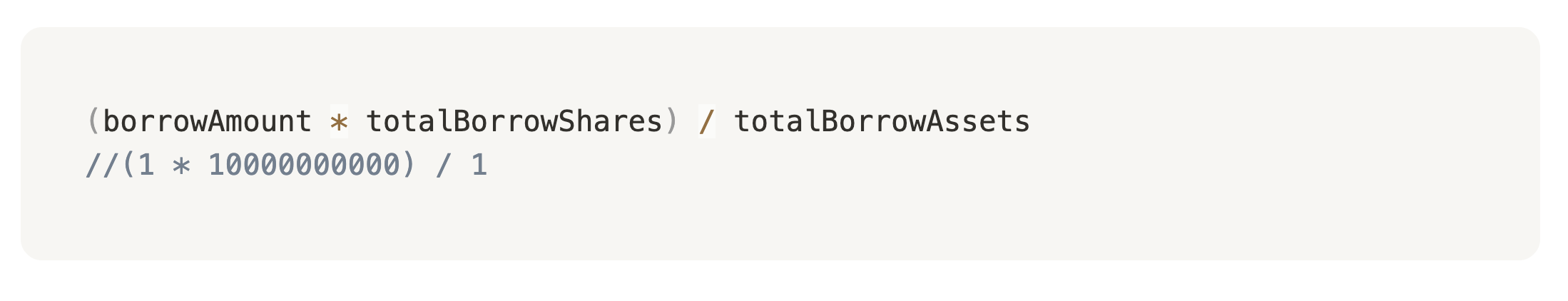
→ Result: huge amount of shares minted
But when repaying, the totalBorrowShares is inversed, thus end up being 0:
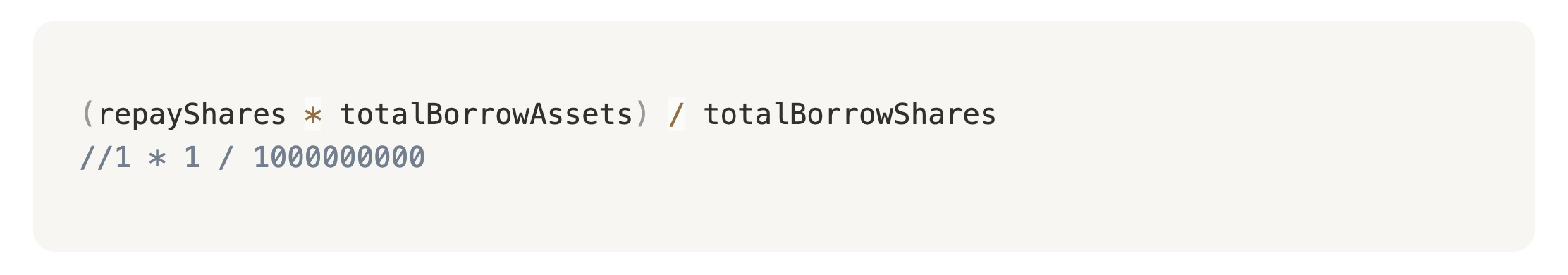
However, the protocol correctly rounds up in it's favour during the repayment.
It means that even if shares to be repaid end up being 0, attacker still pays 1 wei of assets.
It's just for you to note that protocol at this point rounds correctly
→ Value rounds up — attacker pays
1 wei, even if worth less.
Over time, this loop inflates totalBorrowShares massively, while keeping totalBorrowAssets ≈ 1.
5. Final Repay
Attacker does one last repay(1).
Now:
totalBorrowAssets= 0totalBorrowShares= extremely high
6. Second Wallet — Draining the Protocol
From a second address:
Attacker borrows all remaining assets.
Here’s the thing:
Since totalBorrowAssets = 0, this line:
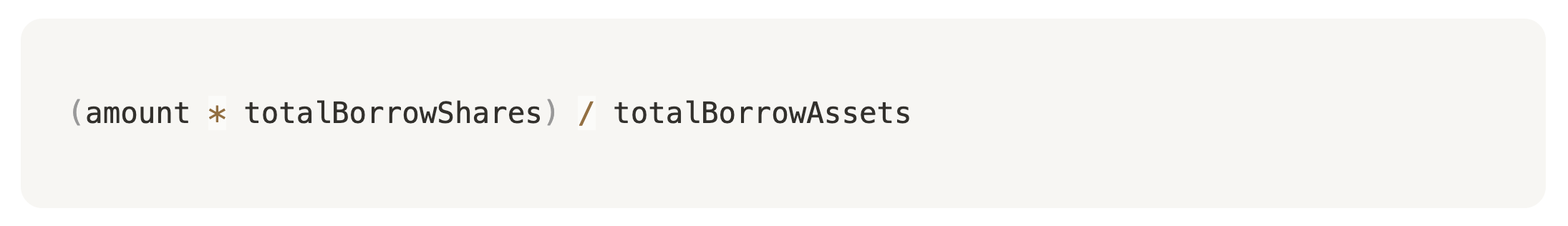
is skipped → protocol just gives 1:1 shares for assets.
Because totalBorrowAssets is 0
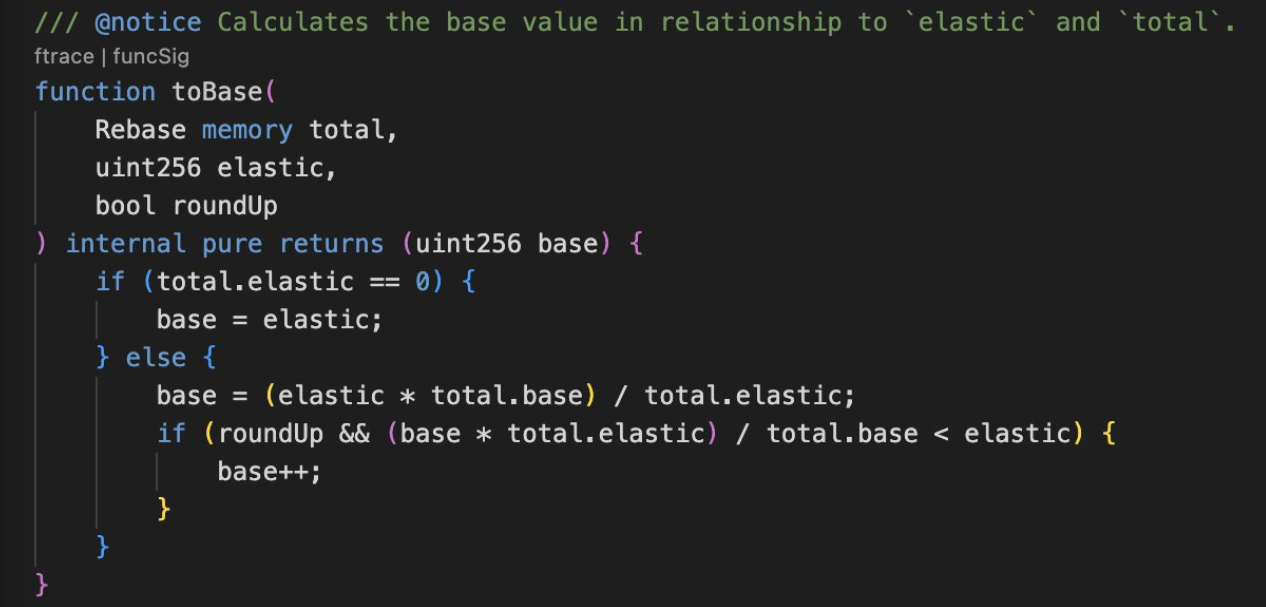
🧠 So attacker gets all funds without reflecting real debt.
⚠️ Health Factor Bypass
Protocol calculates health like this:
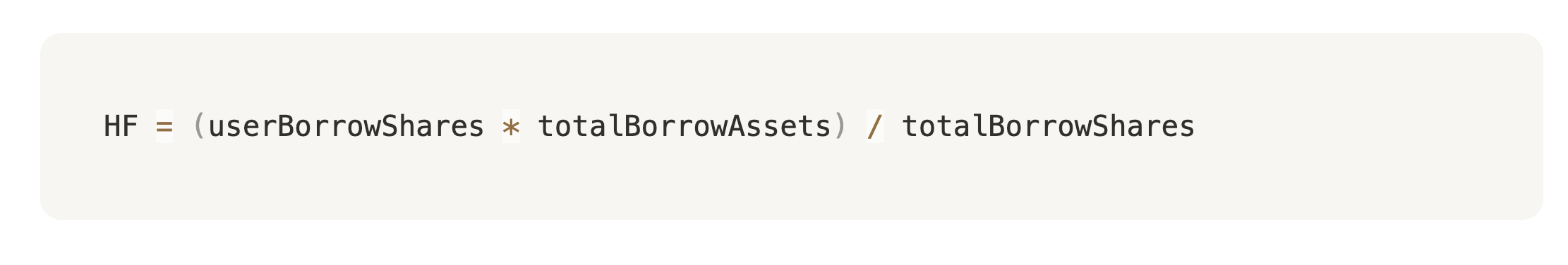
But:
totalBorrowShares= hugetotalBorrowAssets= all funds we borrowed from protocol.
Huge, but not so astotalBorrowShares
Result:
- Health Factor rounds to 0
- Protocol thinks borrower is healthy ✅
Meanwhile, attacker already stole all assets
This kind of exploit shows one thing clearly:
Complex attacks are just a chain of simple steps — executed well.
But at the core?
It usually comes down to one small mistake.
Even if everything else is solid, a subtle misalignment can collapse the whole thing.
In this case, it started when the Vault logic let totalBorrowAssets drop —
while totalBorrowShares stayed untouched.
From there, the attacker used existing mechanics to push values even lower.
Once they got things close to zero, they started abusing rounding — depositing and repaying 1 wei —
to inflate totalBorrowShares to insane levels.
And after that?
Just one step left:
Borrow everything and bypass the health check.