XSS.IS Shut Down: Inside the Raid That Toppled a Cybercrime Powerhouse

Source: XSS.IS Silenced! Inside the investigation that shut down one of cybercrime’s most feared bazaars
Imagine opening your usual dark web forum-where stolen data and malware were traded daily-and seeing a stark message instead of the usual posts: a seizure notice bearing the logos of the French Brigade for the Fight against Cybercrime, the Ukrainian Cyber Intelligence Department, and Europol. The banner bluntly states: “This domain has been seized.”
This marked the end of XSS.IS, a secretive auction site that operated for 12 years as a hub for malware developers, access sellers, and ransomware groups. But this takedown was not just a routine raid-it was a highly sophisticated, four-year international investigation that dismantled one of the most trusted cybercrime platforms.
How the French Investigation Unfolded (2021–2023)
The probe began in July 2021 when the French National Prosecutor’s Office for Cybercrime (JUNALCO) sought to understand how XSS.IS operated openly despite frequent mentions of extortion targeting French businesses.
- The Cybercrime Brigade (BL2C) combed through DNS records, TLS certificates, and mapped hosting servers located in the Netherlands, Russia, and Malaysia.
- A pivotal discovery tied large transactions on XSS to a Jabber domain named thesecure.biz.
- BL2C secured a judicial wiretap to monitor staff chat logs on this server, revealing:
- Administrator work patterns centered in Kiev (9 a.m. to 6 p.m.).
- Bitcoin wallets receiving a fixed 3% commission from escrowed transactions.
By the end of 2023, investigators amassed a mountain of evidence-including IP logs, timestamps, cryptocurrency flows, server snapshots, and encrypted backups stored remotely.
From Online Alias to Real Identity (2023–2025)
Identifying the person behind the alias demanded patience and cross-agency collaboration, with Europol’s European Cybercrime Centre joining the effort.
Key methods included:
- Open-source intelligence and data leaks: Avatars reused on smaller forums, GitHub commits dating back to 2014, and a PGP key created in Kyiv.
- Stylometry analysis: Comparing linguistic style across thousands of posts against confirmed samples, showing a greater than 90% match of writing patterns.
- Financial tracing: KYC data from crypto exchanges uncovered movement from Bitcoin to stablecoins and cash withdrawals matching the suspect’s estimated earnings-over 7 million euros.
These data points led Ukrainian security services (SBU) to an individual living in the suspected Kyiv neighborhood.
The Morning of July 22, 2025: The Raid
At 6 a.m., SBU officers stormed a Kyiv apartment, seizing:
- A Linux laptop
- A Synology NAS
- Two FIDO security tokens
Digital evidence was cloned on-site with Europol’s forensic kits. Handwritten passphrases from a notebook enabled immediate disk decryption. Simultaneously, domain registrars received seizure orders to redirect xss.is traffic to a police-controlled server in Paris displaying the takeover banner.
Traffic to the Jabber server thesecure.biz was also rerouted to a monitored sinkhole, catching affiliates trying to reconnect.
Within two hours, the forum vanished from the web. The alleged administrator, a 35-year-old Ukrainian national, was detained facing charges including criminal conspiracy, extortion, and money laundering.
Investigative Timeline at a Glance
| Year | Milestone | Details |
|---|---|---|
| 2013 | Launch of XSS | Successor to DaMaGeLaB, introduced internal trust scores |
| Dec 2018 | Rebranding as “XSS” | Invitation-only access, paid arbitration service |
| May 2021 | Ban on ransomware discussions | Attempt to lower profile post-Colonial Pipeline attack |
| July 2021 | Investigation launched in France | JUNALCO assigns BL2C the case |
| Aug 2021 | Wiretap on thesecure.biz | Selective monitoring of staff chatrooms |
| 2022-2023 | OSINT and blockchain analysis | Converting aliases to wallet IDs and KYC details |
| Sept 2024 | European-Ukraine Task Force | Europol opens Kyiv mobile unit |
| July 22, 2025 | Raid and domain seizure | SBU arrests and forum taken offline |
The Core of XSS: Escrow Services
XSS distinguished itself by operating a trusted escrow service, where an administrator held funds until both buyer and seller confirmed deal completion.
- Commission fees were flat at 3%, with up to 5% for higher-risk transactions.
- Payments took place exclusively in Bitcoin, with final approvals conducted via Jabber messages.
- Compared to similar forums, XSS featured quick dispute arbitration (within 24 hours) and exclusive “VIP” channels for deals exceeding $50,000.
Dark Web Fallout: thesecure.biz Also Offline
The Jabber server managing XSS’s escrow and dispute operations, thesecure.biz, is unreachable worldwide:
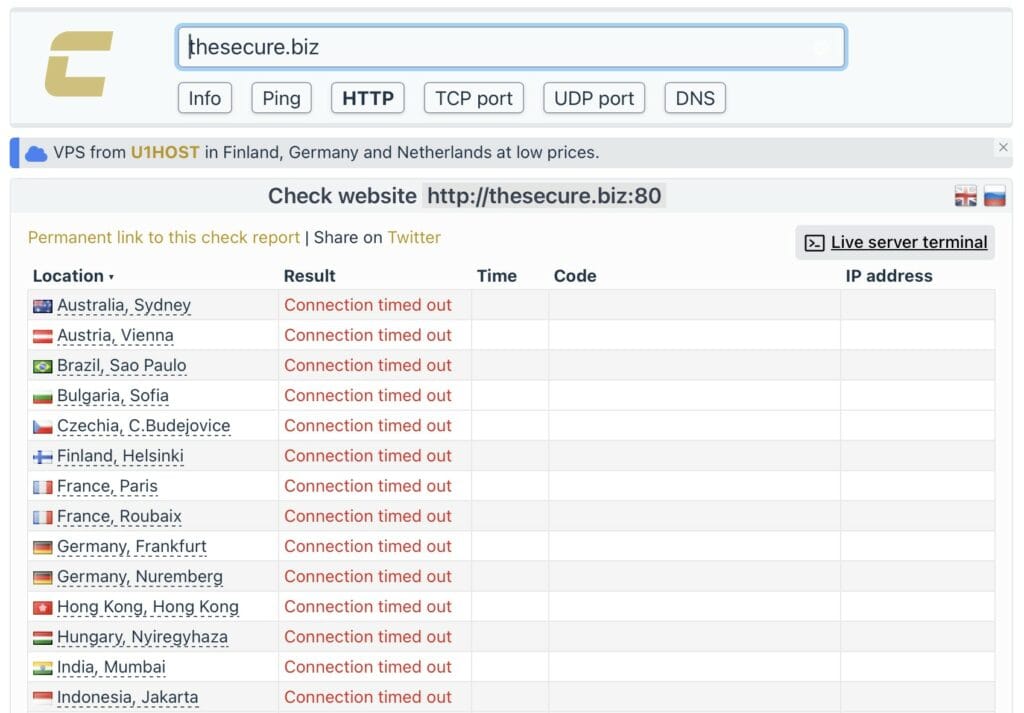
- Testing from numerous locations, from Australia to Finland, shows complete network silence.
- No fallback banners or redirect messages appear, indicating a full shutdown.
Inside the Seized Data Cache
Investigators reportedly retrieved:
- 13 terabytes of forum posts, private chats, and Jabber logs.
- Records of 93,000 escrow transactions since 2019, including wallet addresses and amounts.
- Details from over 1,000 arbitration cases, showing evidence of internal fraud with attached files and PGP-signed documents.
This trove allows law enforcement to:
- Map criminal networks by linking wallets to blacklisted addresses and known laundering schemes.
- Identify ransomware developers, access brokers, and money mules.
- Help incident responders alert victims before attacks unfold, disrupting criminal pipelines early.
Impact on the Dark Web Ecosystem
With XSS offline, criminal trading has spilled over to smaller forums like Exploit and private Telegram groups - but without the escrow “guarantee,” scams and disputes have surged sharply.
This echoes previous collapses such as after the shutdown of Genesis Market (April 2023) and BreachForums (2023-2024), illustrating that without trusted marketplaces, the darknet fragments into less reliable and riskier micro-communities.
What’s Next for Cybercrime Markets?
- Ongoing investigations may use the seizure banner to encourage insiders to cooperate for reduced sentences.
- Criminals are likely to shift towards more private and encrypted platforms like Tox, Matrix “ghost sessions,” and one-on-one Telegram chats.
- Some plan to implement decentralized escrow via smart contracts on anonymous blockchains-but history suggests that without trusted human oversight, such systems rarely endure.
Takeaway
The XSS.IS takedown represents a major blow to the trust infrastructure that powers cybercrime markets. By removing a reliable escrow and arbitration hub, law enforcement forces illicit trade towards fragmentation, making it more vulnerable to infiltration and collapse.
For the full details and ongoing coverage, visit redhotcyber.com


